Security and Privacy Vulnerability Reporting
Security and Privacy Vulnerability Reporting
If you believe you have discovered a security or privacy vulnerability that affects the products (including software, or web servers) of One Retail Group Limited, please report it to us.
If you have inquiries or concerns regarding One Retail Group Limited’s Privacy Policy or data processing practices, you can access further details on our Privacy Policy page or contact our Customer Care Team for additional information and assistance.
How to report a security or privacy vulnerability
If you believe you have discovered a security or privacy vulnerability that affects the products (including software, or web servers) of One Retail Group Limited, please download and fill out the Vulnerability Reporting template. Once complete please email the document directly to [email protected].
What happens next
After the submission of the report, One Retail Group Limited will undertake efforts to authenticate the disclosed vulnerability. Should further information be necessary for validation or replication purposes, our team will collaborate with you to acquire it. Upon conclusion of the initial investigation, findings will be communicated to you, accompanied by a resolution strategy, and, if necessary, a discussion regarding public disclosure.

Vulnerability Handling Process
One Retail Group Limited handles reported vulnerabilities according to its Vulnerability Management Protocol.
Response Scope
This Vulnerability Management Protocol applies to all hardware, software products or services provided by One Retail Group Limited, including cloud platforms, apps or mini-programs on mobile phones, and hardware, software, and firmware of home appliances.
Vulnerability Management Protocol
One Retail Group Limited is committed to enhancing the safety of its products and fully supports the secure operation of its customer networks and businesses. We place great importance on vulnerability management in product development and maintenance and have established a complete vulnerability handling process to enhance product safety and ensure timely response when vulnerabilities are discovered or reported.
Below is an overview of our vulnerability handling process, illustrating the key steps from vulnerability reporting to closure and disclosure.
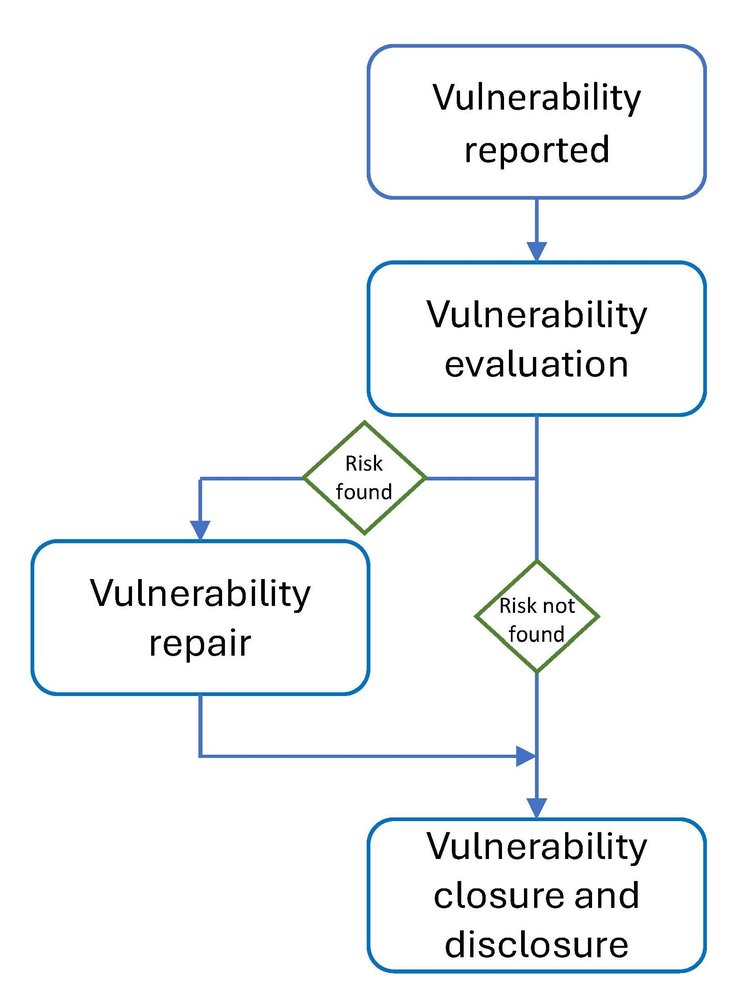
- Vulnerability reported: Upon receipt of a security or privacy vulnerability case, One Retail Group Limited commences procedures to authenticate the disclosed vulnerability.
- Vulnerability evaluation: The security team conducts analysis and verification of vulnerabilities, assessing their severity. Should further information be necessary to validate or replicate the vulnerability, collaboration with the reporter is initiated to obtain it.
- Vulnerability repair: Upon confirmation of a vulnerability, comprehensive remediation plans, including mitigation measures and patch deployment strategies, are developed. In cases where a patch or fix is not required, alternative measures will be taken to ensure security.
- Vulnerability closure and disclosure: Following the completion of the investigation, findings will be communicated to the vulnerability reporter, accompanied by a proposed resolution strategy and, if relevant, discussions regarding public disclosure.
Confidentiality Mechanism
During the vulnerability handling process, One Retail Group Limited’s security team will rigorously manage the scope of vulnerability information, sharing it only with relevant personnel directly involved in addressing the vulnerability. One Retail Group Limited has implemented the necessary measures to safeguard the acquired data in compliance with legal and regulatory standards. Unless explicitly requested by affected customers or mandated by law, such information will not be shared or disclosed to third parties without prior consent of the vulnerability reporter.
Severity Assessment of Vulnerabilities
Based on the comprehensive score of the Security Severity Rating (SSR) vulnerability severity level assessment, One Retail Group Limited classifies vulnerabilities into five levels: Critical, High, Medium, Low, and Informational.
Critical-level security issues
- Directly obtaining core system privileges. These vulnerabilities can directly jeopardize the internal network and may include, but are not limited to, command execution and remote overflow.
- Vulnerabilities that can obtain a large amount of user core data.
- Logic vulnerabilities that directly cause serious impact. Related vulnerabilities include but are not limited to serious logic errors, vulnerabilities that can cause significant losses to the company and users.
High-level security issues
- Vulnerabilities that allow direct access to business server permissions, including but not limited to arbitrary command execution, webshell uploads, and arbitrary code execution.
- Vulnerabilities that directly result in serious information leaks, including but not limited to SQL injection vulnerabilities in core databases.
- Logic vulnerabilities that directly result in significant impact, including but not limited to vulnerabilities that allow arbitrary changes to account passwords.
- Vulnerabilities that could lead to mass theft of user identity information, such as SQL injection.
- Unauthorized access, including but not limited to bypassing authentication to access the backend.
Medium level security issues
- Vulnerabilities that require interaction to obtain user identity information, including but not limited to stored XSS vulnerabilities.
- Arbitrary file operation vulnerabilities, including but not limited to arbitrary file reading, writing, deletion, downloading, etc..
- Unauthorized access, such as bypassing restrictions to modify user information or execute user operations.
- Relatively serious information leakage vulnerabilities, including the leakage of sensitive information files (such as DB connection passwords).
Low level security issues
- Vulnerabilities that can cause certain impacts, but do not directly affect device permissions or data security. These may include minor information leakage, URL redirection, less exploitable XSS vulnerabilities, and common CSRF vulnerabilities.
Information-related issues
- Bugs that do not involve security issues, including but not limited to product function defects, webpage garbled code, style disorder, static file directory traversal, application compatibility issues, etc..
- Vulnerabilities that cannot be exploited, such as CSRF without sensitive operations, meaningless abnormal information leakage, internal IP address/domain name leakage.
- Other issues that do not directly indicate the existence of vulnerabilities, such as issues based purely on user speculation.
Third-party software vulnerabilities
Due to the diversity of integration methods and scenarios of third-party software/components in One Retail Group Limited products, the company will adjust the vulnerability rating of third-party software/components according to the specific scenarios of the product to reflect the true impact of the vulnerability. For example, if an affected module of a certain third-party software or component is not in use, the associated vulnerability would be considered ‘unexploitable and unaffected’. If the existing evaluation system cannot cover the dimensions of evaluation, One Retail Group Limited is responsible for explaining the evaluation results.
If the following three criteria are met at the same time, One Retail Group Limited will identify the vulnerability as “High Profile”:
01 CVSS score is 5.0 or above.
02 The vulnerability has attracted widespread public attention.
03 The vulnerability is likely or already has available exploits and may or is being actively exploited.
For “High-Profile” third-party vulnerabilities, One Retail Group Limited conducts thorough assessments across all product versions. Upon confirming the severity of the vulnerability as ‘High-Profile’, we promptly issue Security Notices (SN) to inform relevant customers of our handling process. In cases where a vulnerability patch solution is available, One Retail Group Limited offers risk decision-making and mitigation support to affected customers through Security Announcements (SA). For third-party vulnerabilities not classified as “High-Profile”, the company will provide explanations within version/patch instructions.
Release of Vulnerability Information Notice
One Retail Group Limited discloses security vulnerabilities in its product(s) through two primary methods:
- Security Advisory (SA):When a vulnerability is confirmed, we disclose detailed vulnerability information and corresponding remediation measures through an SA.
- Security Notification (SN): When a potential vulnerability is discovered or noticed externally, but not yet confirmed, we disclose basic information about the vulnerability and our investigation progress through an SN. Vulnerability information should be kept confidential until One Retail Group Limited releases a security advisory or security notification to the public.
Announcement Plan
When one or more of the following conditions are met, One Retail Group Limited will release an SN or SA to provide customers with real-time risk decision support:
- The Security Severity Rating (SSR) is defined as “Critical” or “High” vulnerabilities. One Retail Group Limited has completed the vulnerability response process and can provide vulnerability patch support to customers to reduce real-time risks.
- One Retail Group Limited prioritises response acceleration for vulnerabilities in product versions that may attract widespread public attention, are actively exploited, or could increase risk to our customers. Upon meeting these conditions, One Retail Group Limited promptly notifies customers and provides continuous updates on the vulnerability response progress.
Security Update
Please update your applications and devices in a timely manner, as this is one of the most important measures to maintain the security of One Retail Group Limited products. Obtain the latest software updates from the official website:
- https://play.google.com/store/apps/details?id=com.ictp.active&hl=en&gl=US
- https://apps.apple.com/gb/app/active-era/id1458687778
For specific product/software version vulnerability fixes, please refer to the announcement: jump to the security notice page.
Disclaimer & Reservation of Rights
- The policy outlined in this document does not constitute a guarantee or contractual obligation, and it remains subject to change at the discretion of One Retail Group Limited.
- One Retail Group Limited reserves the right to amend or update this document at any time. We commit to revising this policy statement as necessary to enhance transparency or respond more actively to feedback from customers, regulatory agencies, industries, or other stakeholders, including:
- Changes to the overarching policy.
- Introduction of best practices, etc.
- Upon publishing changes to this policy statement, the “Update Date” at the bottom of this policy will be revised accordingly.
Definition
The following definitions are used in this strategy:
Name | Definition |
Vulnerability | A weakness in a system or product that could be exploited by attackers to compromise its security. |
Security Severity Rating (SSR) | A classification system used to assess the severity of security vulnerabilities. |
Common Vulnerability Scoring System (CVSS) | A framework used to assign a severity score to computer security vulnerabilities. |
Security Advisory (SA) | Detailed information provided to users about a security vulnerability in a product, along with guidance on how to mitigate the risk. |
Security Notification (SN) | Basic information provided to users about a potential security vulnerability in a product that has not yet been confirmed, along with updates on the investigation progress. |
Online Risk | Refers to the various security threats present on the internet, including cyber-attacks, data breaches, phishing attempts, malware infections, and identity theft. Mitigating online risks involves implementing preventive measures such as using strong passwords, updating software regularly, installing antivirus solutions, and being cautious about sharing personal information. |
Security Notice
Security Bulletins
At present, there are no identified safety or privacy vulnerabilities or risks associated with One Retail Group Limited product(s).
We remain committed to ongoing monitoring, and should any vulnerabilities or risks be detected, we will promptly issue security announcements and notifications. These communications will comprehensively outline newly identified security vulnerabilities, their potential impacts, and recommended solutions, ensuring clarity regarding the security status of our product(s).




